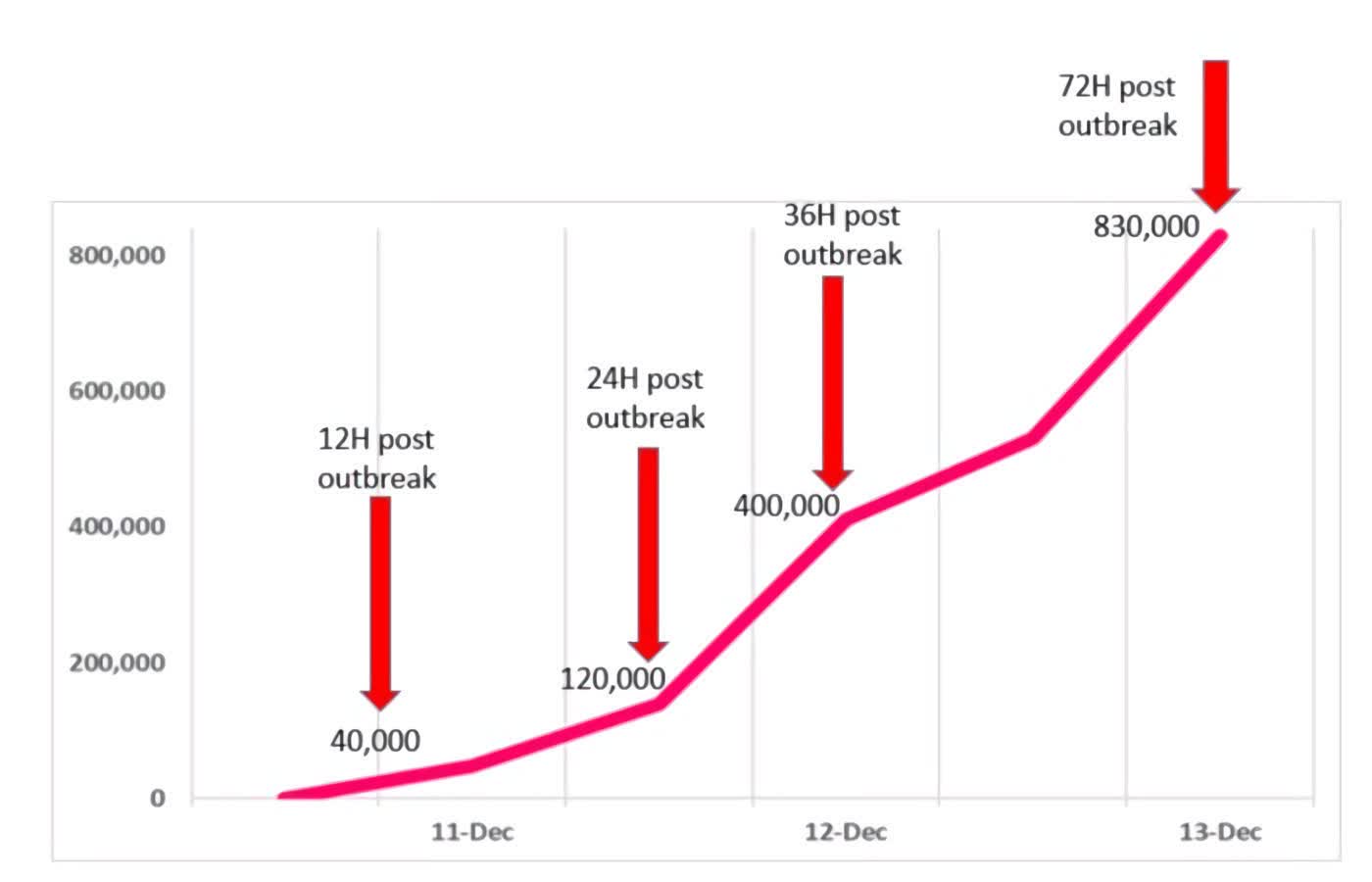
What just happened? On Tuesday, security researchers revealed that hackers had employed the recently discovered Log4J exploit in over 840,000 cyberattacks. Bad actors have targeted companies worldwide, including big-name players like Apple, Amazon, IBM, Microsoft, and Cisco.
Techspot reported on Log4J over the weekend after it was discovered last week. Since Friday, the open-source software's use has become a pandemic in its own right. Security firm Check Point has been monitoring the situation and, at one point, were seeing more than 100 Log4J attacks per minute.
The hackers are scattered globally, but many seem to be coming from state-sponsored groups out of China, cybersecurity company Maniant CTO Charles Carmakal told Ars Technica. Other firms tracking the attacks, including Check Point and SentinelOne, confirm that many are from known Chinese hackers. Check Point adds that more than half of the exploits come from well-known hacking groups using it to deploy common malware like Tsunami and Mirai for botnets and XMRig to mine Monero.
Researchers initially discovered the exploit on Minecraft servers. It uses a flaw in Java to launch remote code execution attacks that can fully take control of a system. LunaSec noted that the Apache Struts framework, used on thousands of business servers, was particularly susceptible.
"[This vulnerability is] one of the most serious I've seen in my entire career, if not the most serious," the Director of the US Cybersecurity and Infrastructure Security Agency (CISA) Jen Easterly told industry leaders. She added that the flaw could impact hundreds of millions of devices.
Check Point noted that hackers exploiting Log4J used it to take over computers to perform anything from mining cryptocurrency to sending spam to initiating DDoS attacks with large botnets.
The UK's National Cyber Security Centre and the US CISA have strongly urged companies to make patching out this severe vulnerability their top priority. The leading brand companies previously mentioned are hurrying to issue fixes, and so far, none have reported having any breaches. However, IT administrators should not underestimate the seriousness of the situation.
"With this vulnerability, attackers gain almost unlimited power---they can extract sensitive data, upload files to the server, delete data, install ransomware, or pivot to other servers," said Acunetix's head of engineering, Nicholas Sciberras.
Image credit: Cyber Security by Ecole Polytechnique (CC BY-SA 2.0), Log4J Attacks by Check Point
